Cyber Security Ciso Dashboard

Providers typically offer customers a number of customizable solutions but this variety begs the question.
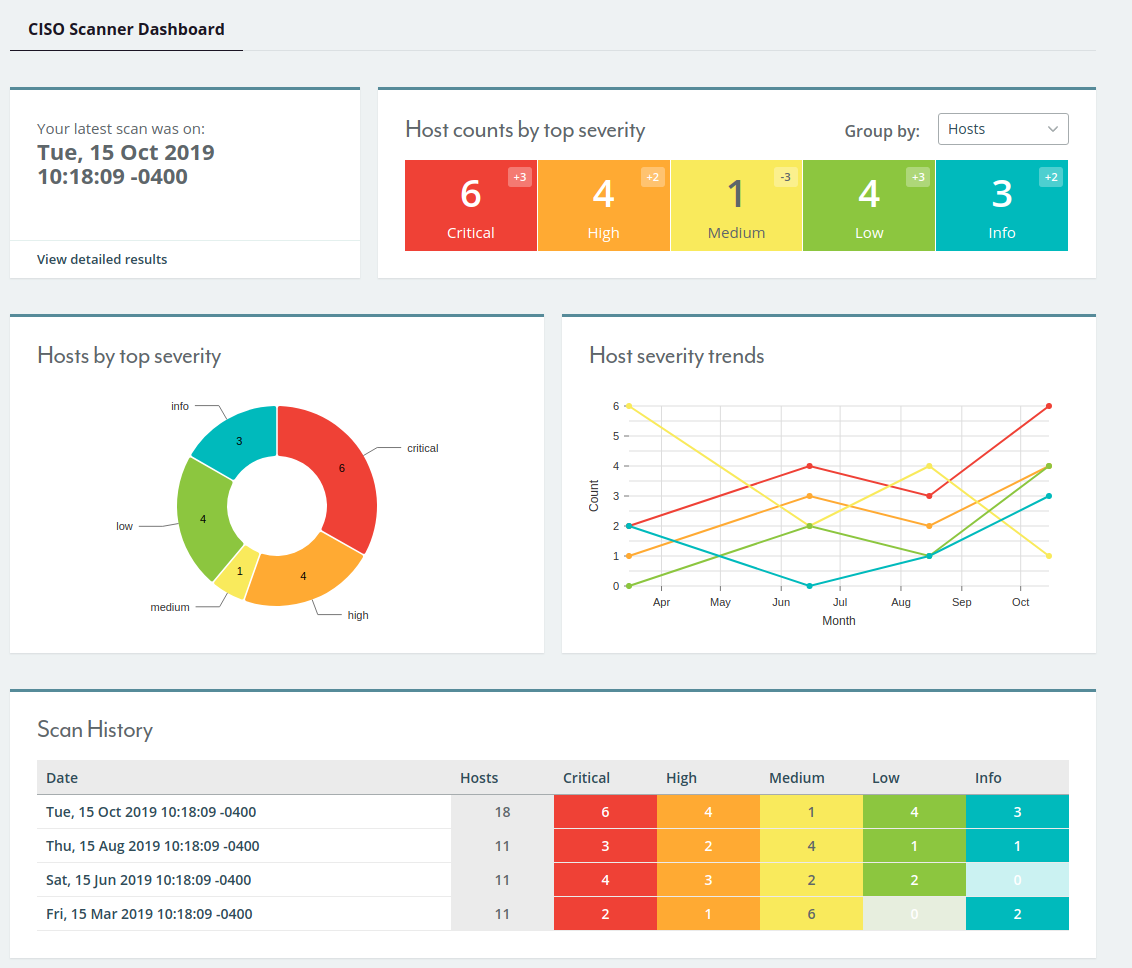
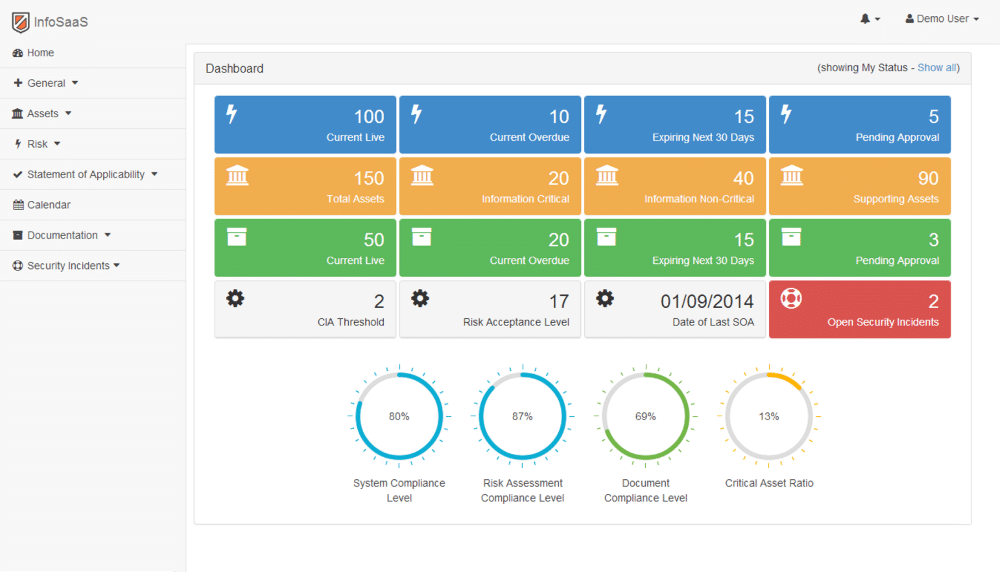
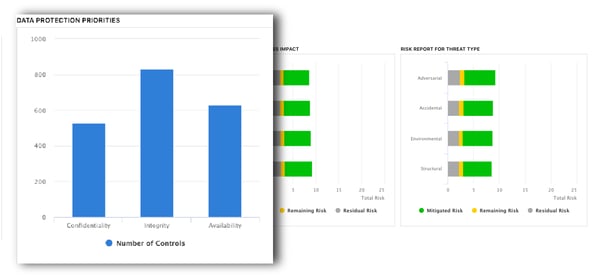
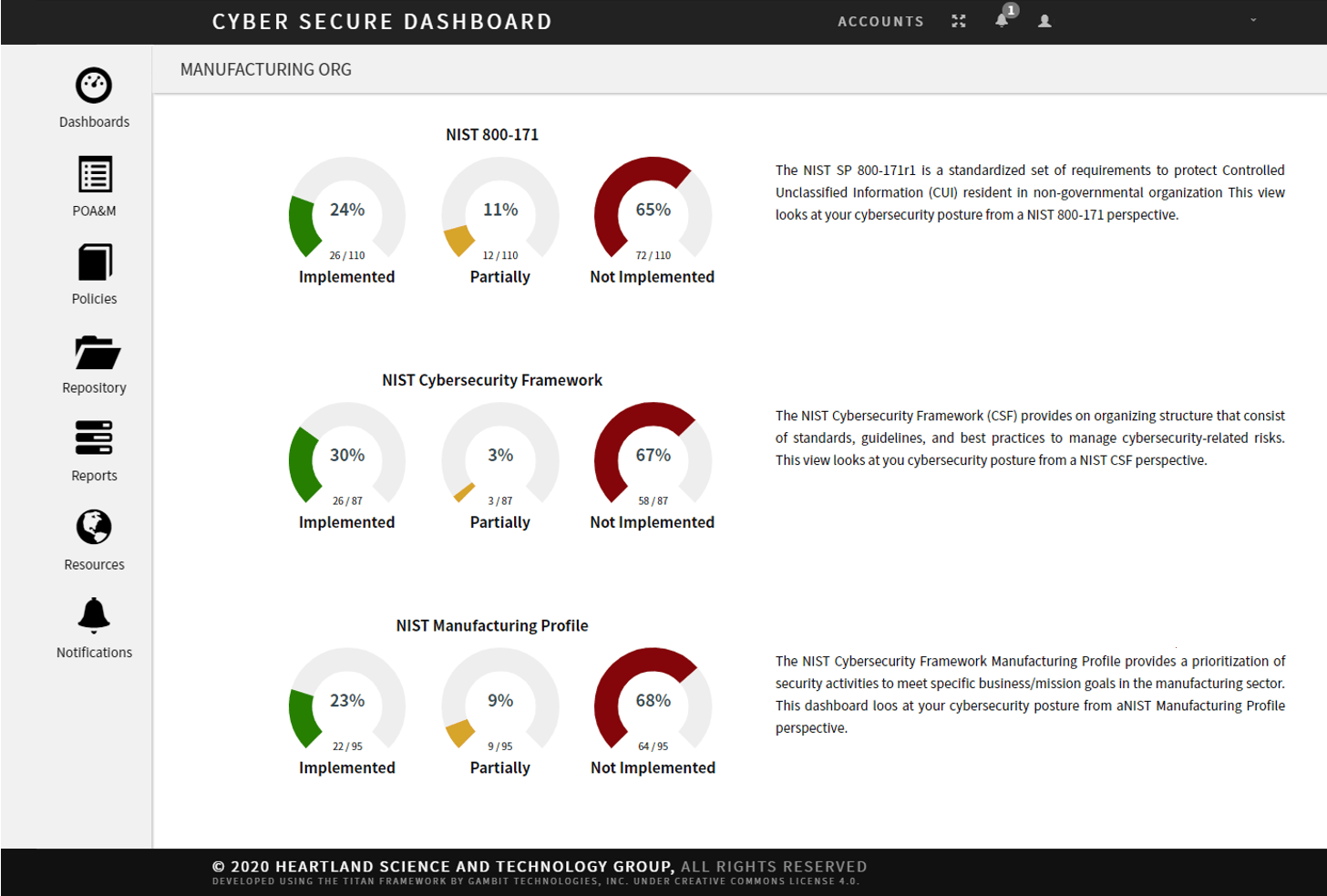
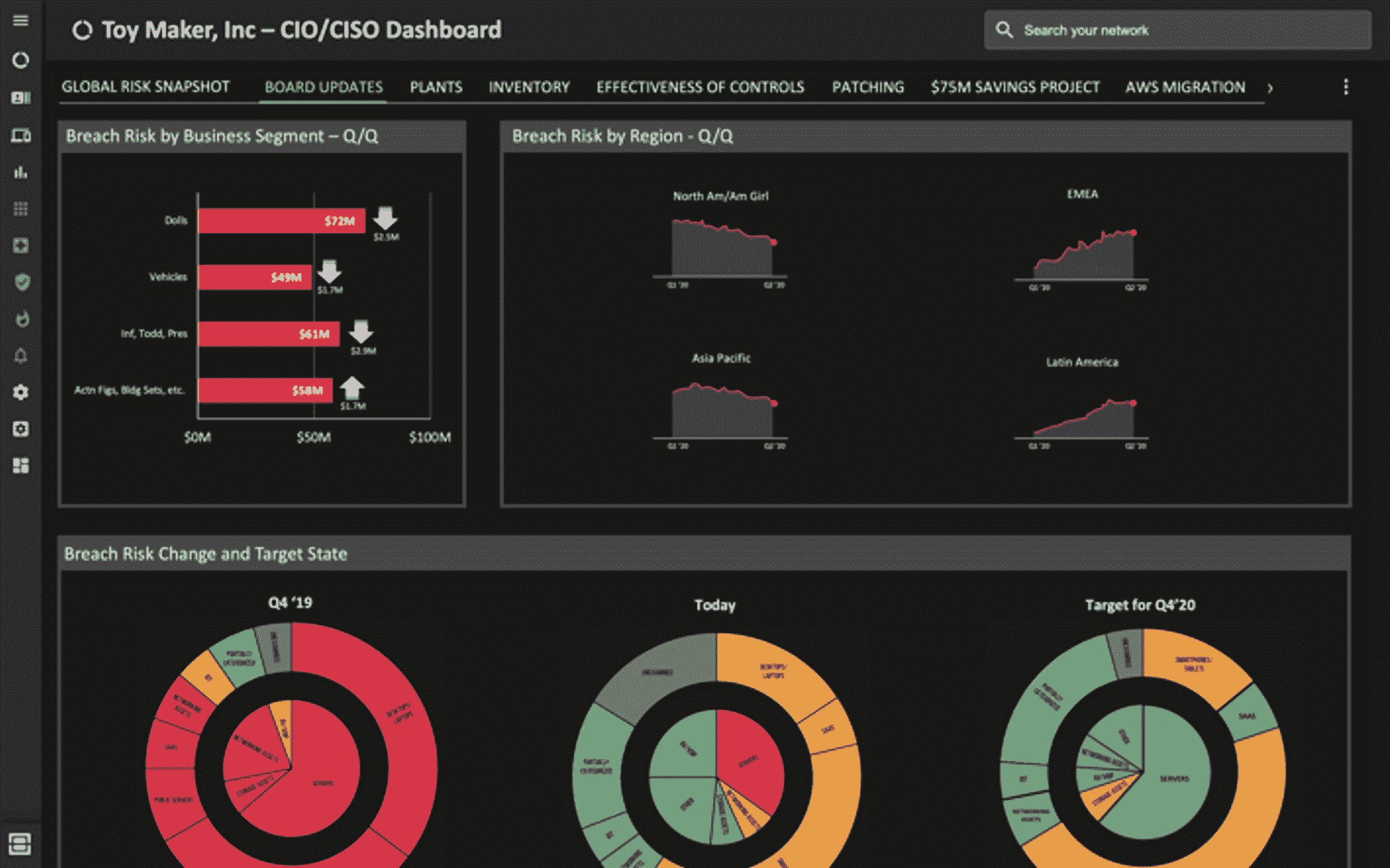
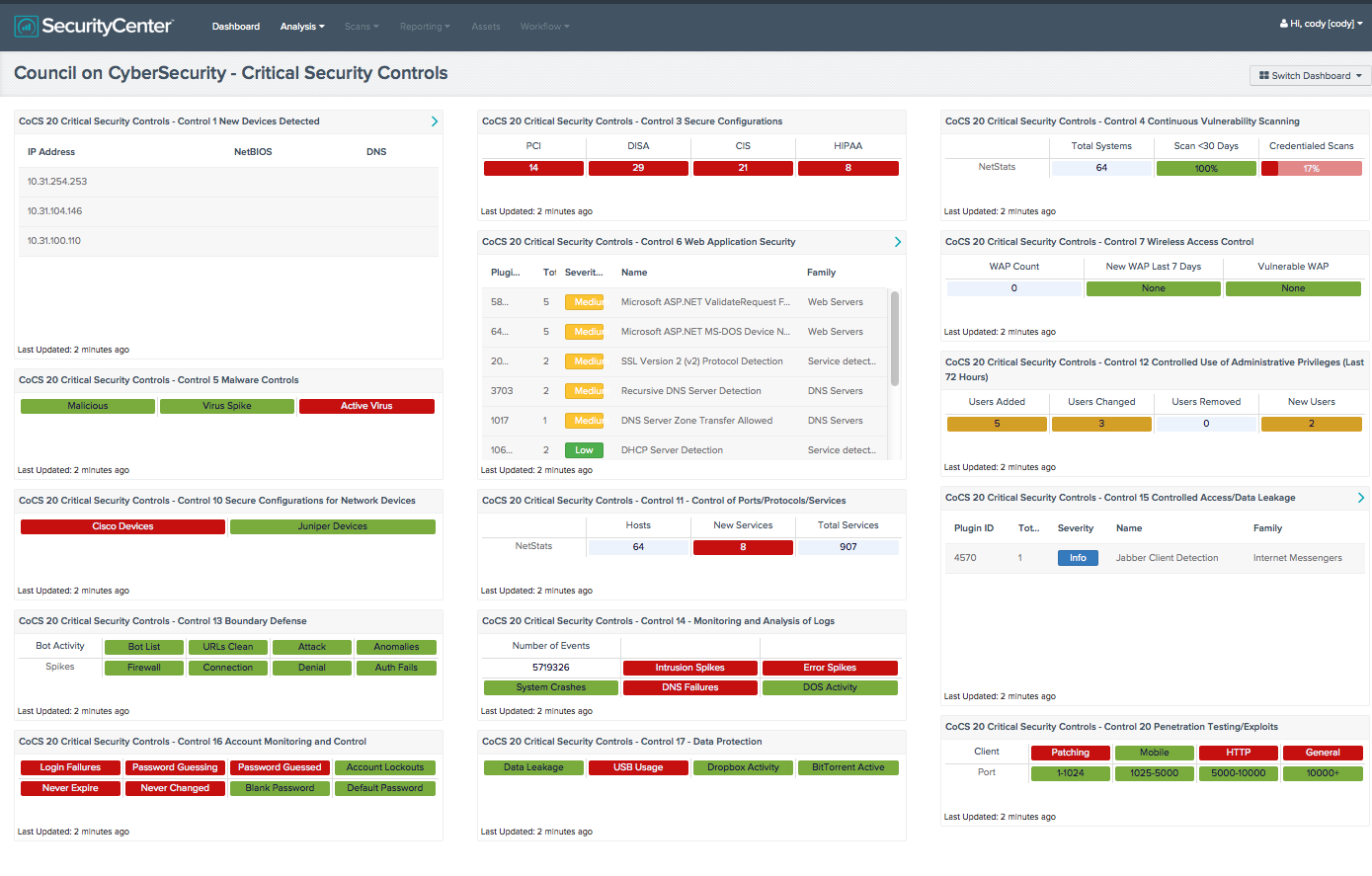
Cyber security ciso dashboard. What the dashboard tracks. As much of a security issue as they create cloud based collaborative tools can be a huge driver for shared working and a bonding tool. Their purpose is to enable better faster decisions to avert threats and increase an organization s overall resilience. How secure is our organization.
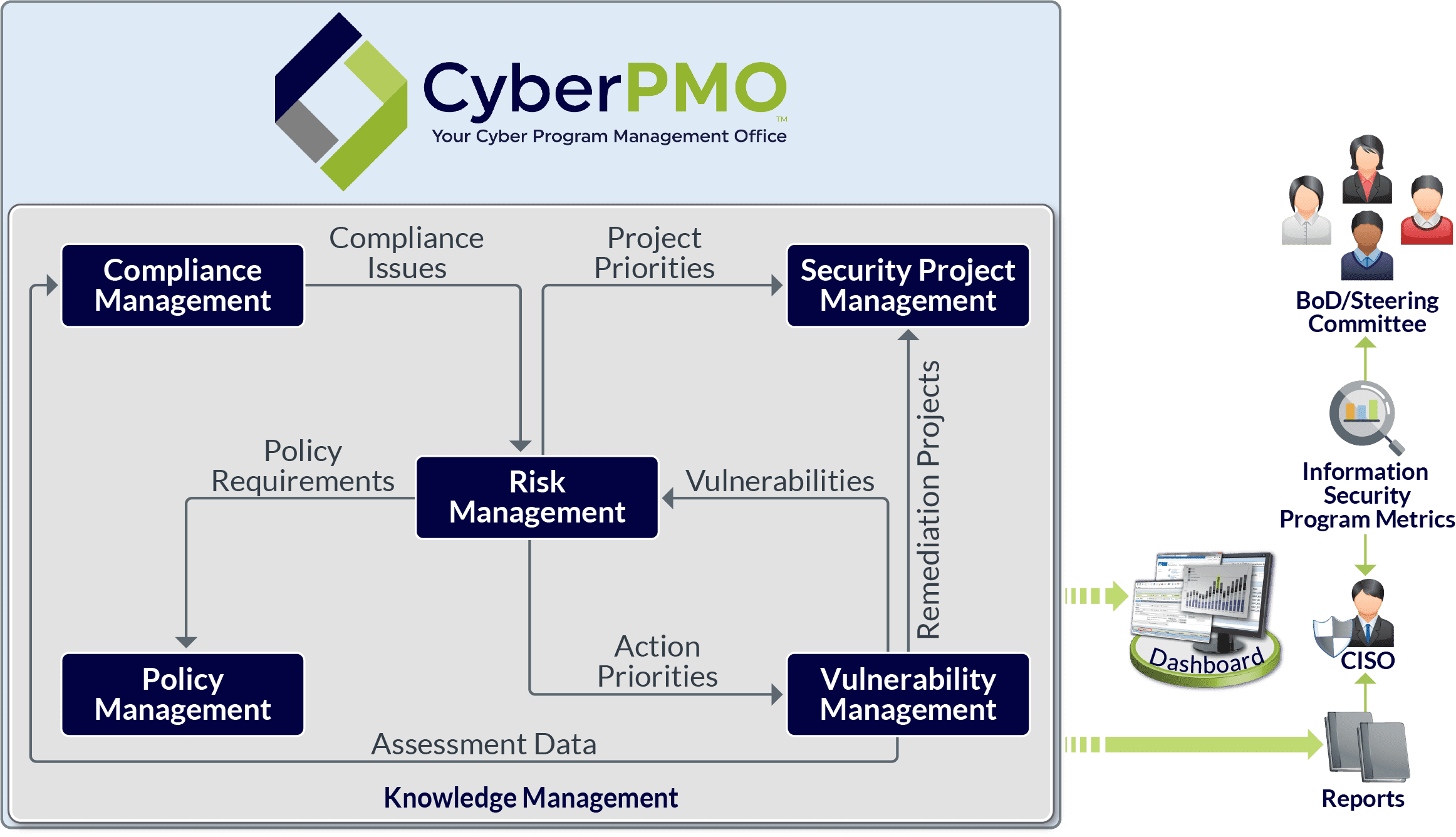
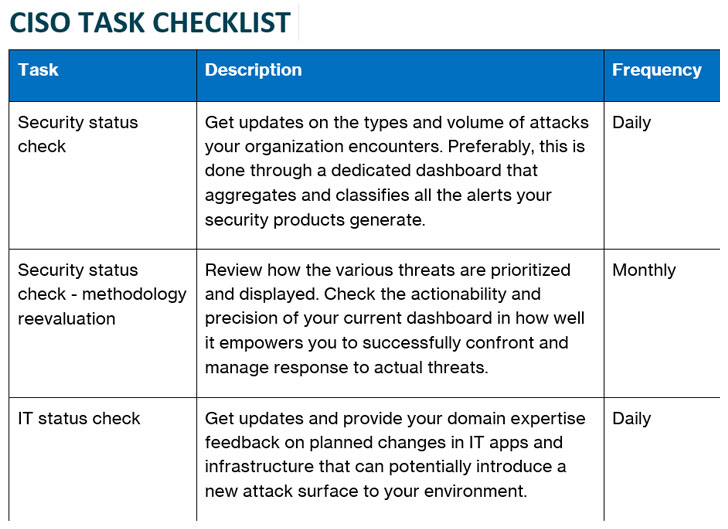
More often than not ciso s and their top lieutenants spend great amounts of time analyzing decision making and performance of their cybersecurity program and need a fast way to measure progress from a high level and reach a common understanding enter the executive dashboard. The chief information security officer ciso is expected to have technologies and security controls in place that reduce the organization s risk as well as processes to monitor the. By enabling multiple levels of drill down into specific areas location of risk and providing real time status updates on the ongoing security operations. Cso offers the latest information and best practices on business continuity and data protection best practices for prevention of social engineering scams malware and breaches and tips and.
What features make a security dashboard most effective. The ciso who excels in 2020 is one who adapts to this situation and finds innovative new ways to collaborate and build relationships with their charges on digital platforms and in other creative ways. The dashboard must be built upon data that are relevant up to date vetted for quality and aggregated in meaningful ways. The dashboard also supports the other s ciso challenges the ciso visibility gap and cyber security priority gap.
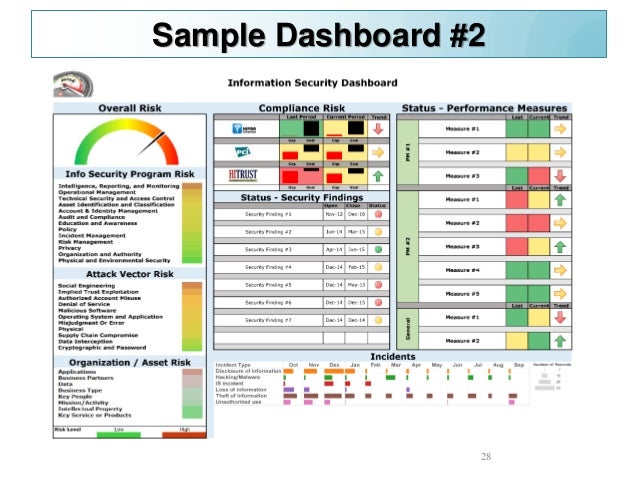
An effective security dashboard provides personnel ranging from security analysts to cisos with the tools to report on incidents and evaluate security risks. And more cios and cisos are coming to depend on their security dashboards to plan strategies and tactics. They showcase everything a cio or ciso needs to know about their security posture. This is where a security dashboard comes in.
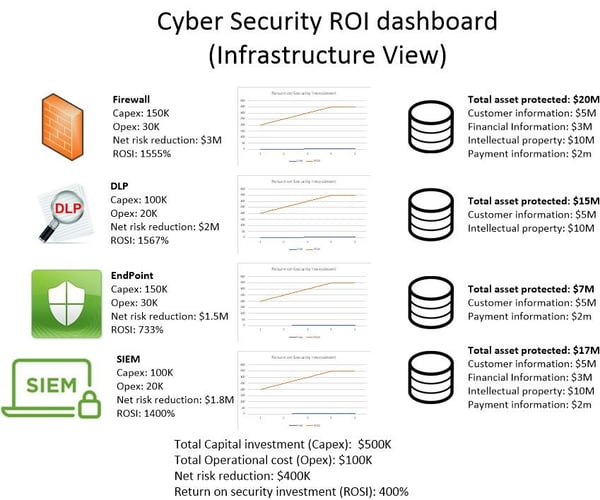
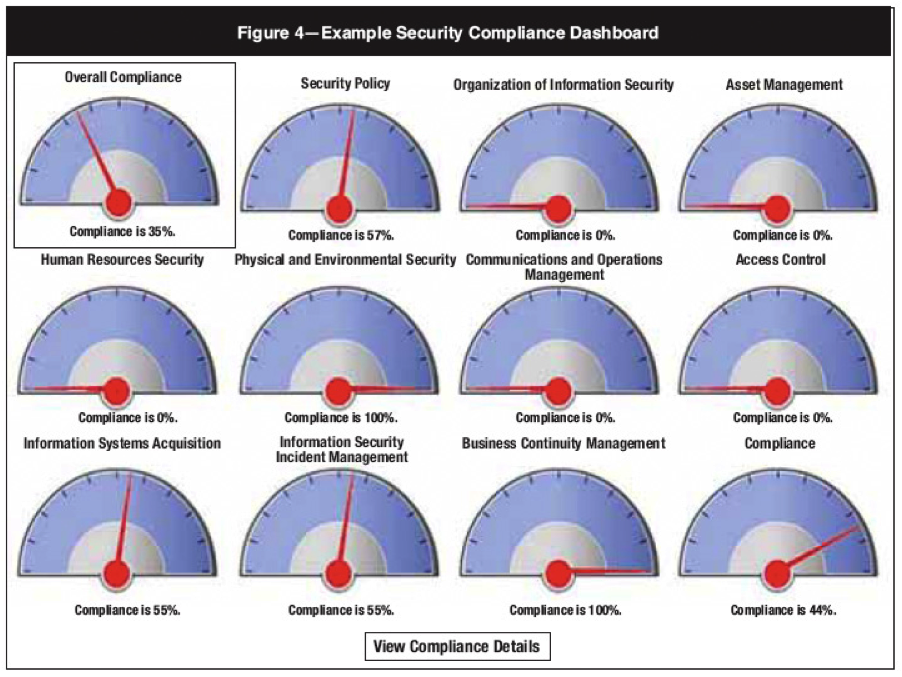
It can be challenging to communicate the value of cyber security in business terms are cyber security services delivered in a fashion that meets business needs. Our clients include cyber insurance companies and brokers automobile manufacturers banks and credit unions software developers security solution providers health care. Risk based security is honored to serve the vulnerability and cyber risk intelligence needs of organizations both large and small across a broad array of industries. Page 5 23 november 2018 cybersecurity metrics dashboards are our security investments paying off.